1. Make Passwords Long
Password length is a primary factor in characterizing password strength. Passwords that are too short or are commonly used words and phrases are vulnerable to brute force attacks.
– NIST (National Institute of Standards and Technology)
– Reformed hacker Kevin Mitnick recommends 20-25 characters
– Think of a phrase that is easy to remember.
1. Something that sticks out to you (perhaps from your favorite book, poem, or song).
2. Create a phrase about your home, family, or hobbies.
3. Create a humorous, nonsensical phrase that’s easy for you to remember
– Take the first letter of each word in your phrase to create the string of characters that will become your password
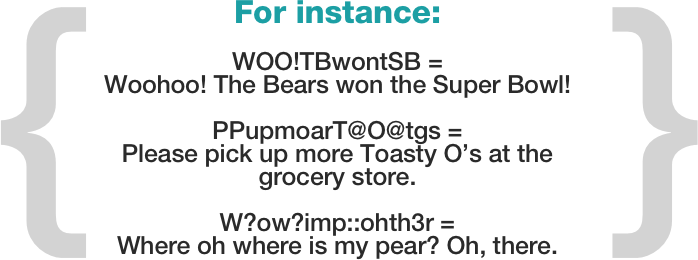
1. “O swear not by the moon, the inconstant moon that monthly changes in her circled orb” from Romeo and Juliet becomes “Osnbtmtim”.
– Add numbers and mix upper- and lower-case letters to add complexity.
1. “Osnbtmtim” can also become “0snbtMt1M” by substituting a zero for the initial letter “O,” changing the two “m’s” for moon into upper-case letters, and swapping out the number one for the letter “i.”
2. The password is still memorable enough to remember, but it is now much harder for a hacker to crack.
– Dictionary words (of any language)
– Words that are spelled backwards, commonly used misspellings, or any abbreviations
– Sequences or repeated characters (e.g., 1234567, abc123, qwerty)
– Personal information such as your name, date of birth, home address, etc.

Once a password is compromised, it can be exploited at any point in time, even years later, as Zuckerberg found out. Reusing a password re-opens the vulnerability window for that password.
The one account of Zuckerberg’s that didn’t get breached was his Instagram, and that’s because “Instagram’s security systems prevented that account from being accessed.” This could refer to a few things, but it likely means that the two-factor authentication (2FA) Instagram set up was enabled for his account.
 Probably one of the most important mechanisms available, 2FA, as its name implies, prevents the compromise of a single authentication factor (the password) from compromising the account. The mechanism typically works by requesting the traditional login information, then sending a confirmation to a device, usually a smartphone, such as a text, phone call, or in-app security verification screen. Ideally, only the authorized person has access to the linked smartphone and can then accept or reject the authentication requests as necessary. More advanced mechanisms can require bio-authentication, such as a fingerprint swipe, which prevents lost or stolen phones from being used to falsely issue confirmations. Most cloud apps offer 2FA now, with many traditional applications following suit. It’s worth the few extra seconds it takes at login to know that even if your password is hacked, no one will be able access your accounts.
Probably one of the most important mechanisms available, 2FA, as its name implies, prevents the compromise of a single authentication factor (the password) from compromising the account. The mechanism typically works by requesting the traditional login information, then sending a confirmation to a device, usually a smartphone, such as a text, phone call, or in-app security verification screen. Ideally, only the authorized person has access to the linked smartphone and can then accept or reject the authentication requests as necessary. More advanced mechanisms can require bio-authentication, such as a fingerprint swipe, which prevents lost or stolen phones from being used to falsely issue confirmations. Most cloud apps offer 2FA now, with many traditional applications following suit. It’s worth the few extra seconds it takes at login to know that even if your password is hacked, no one will be able access your accounts.
![]() You can use a password manager to store your passwords for you. Password managers usually come with a password. These tools use a random number generator with a list of criteria, such as the minimum length of characters required and use of numbers/symbols, to create a new password. This solution is far more difficult to crack than a passphrase.
You can use a password manager to store your passwords for you. Password managers usually come with a password. These tools use a random number generator with a list of criteria, such as the minimum length of characters required and use of numbers/symbols, to create a new password. This solution is far more difficult to crack than a passphrase.
Use a combination of words from different languages if you’re multilingual. You can mix words from different languages and use their phonetic spelling in English to construct your passwords.
This way, you do not have to worry about the keyboard having Unicode characters or system recognizing them. And by compiling languages, you are making the password near impossible to crack via brute force, if the password length is long enough.





