We’ve recently added Sysmon 13 support to our Cyences App in order to detect some of the latest malware/ransomware techniques [Mailto/defray777 ransomware, TrickBot, and BazarBackdoor].
Sysmon 13 lets us monitor the activity of Windows 10 processes and can now detect process hollowing or process herpaderping techniques which would normally not be visible in Task Manager.
Process hollowing is when malware launches a legitimate process in a suspended state and replaces legitimate code in the process with malicious code. This malicious code is then executed by the process with whatever permissions are assigned to the process.
Process herpaderping is where malware modifies its image on the disk to look like legitimate software after the malware is loaded. When security software scans the on-disk file, it will see a harmless file while the malicious code runs in memory.
Below is one of the sample events from Windows Win-Event-Viewer:
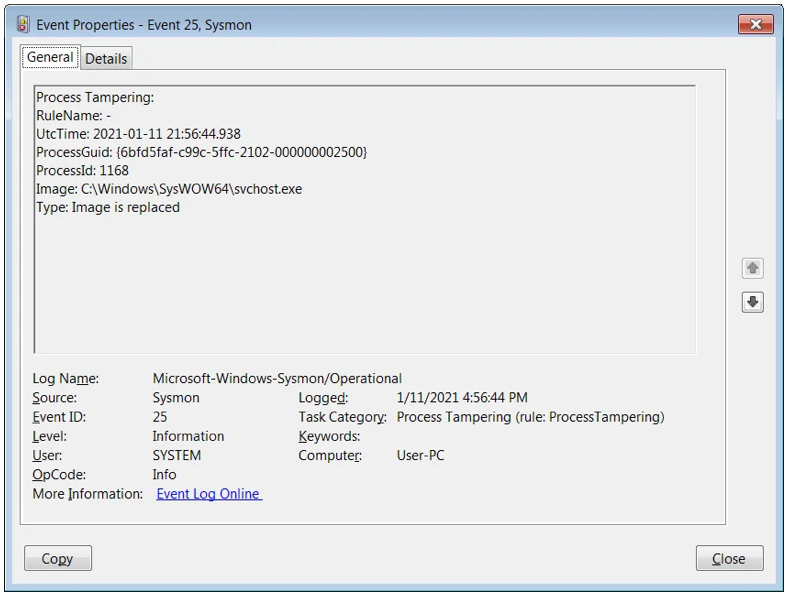
This new alert will detect malicious activities and communicate their presence through Splunk, providing helpful dashboards to create a forensic report of the incident.
References
Read the App’s Documentation
(App Installation/Configuration and Sysmon data collection guide)
Written by Usama Houlila.
Any questions, comments, or feedback are appreciated! Leave a comment or send me an email to uhoulila@cr.jlizardo.com for any questions you might have.




