Since the beginning of the COVID-19 lockdown, we have witnessed an astonishing amount of attacks launched against remote workers. More and more companies have begun to pay perpetrators through a financial windfall that have allowed them to add more programmers to launch even more sophisticated attacks. Ransomware has become a full-on war than a skirmish.
Although there is no magic bullet to achieve resolution, we can utilize existing technologies to prevent and slow this parallel epidemic. Our focus is on addressing the entire pyramid of pain (David Bianco) and will be creating solutions for each level although not in any specific order.
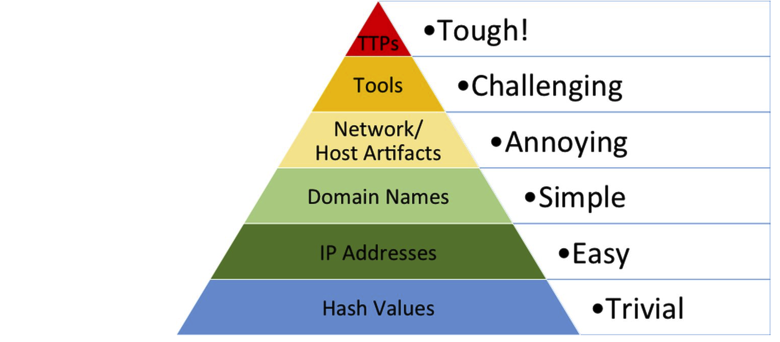
For this post, we will start putting together the orchestration tools available on Splunk to detect common patterns that ransomware follows, looking specifically for this blog at four key tactics (Common File Extensions, Common Ransomware notes, High number of file writes, and wineventlogclearing) These are based on MITRE ATT&CK ransomware detection techniques. If you work in this field, we welcome your opinion and insights.
To start, we assume that your environment has the following:
- Enterprise Security (optional)
- If you have Enterprise Security (ES), you can use the correlation searches available for security incidents, but you can alternatively create alerts without having ES. Note: You must update some of the macro definitions – see at the end of the post.
Splunk Common Information Model
- The Common Information Model (CIM) add-on contains a collection of preconfigured data models that you can apply to your data at search time.
ES Content Update App
- This is a Splunk App that provides regular Security Content updates to help security practitioners address ongoing time-sensitive threats, attack methods and other security issues. Queries here use some macros that come built-in with ES.
Common file extension detection
This tactic will determine if there are any known ransomware file extensions present in the environment. Although the ransomware extensions can be changed in future attacks, similar to virus detection, all previous incidents should be carried forward.Thought Process
- This detection query is based on the Filesystem dataset from the Endpoint data model.
- There is a lookup of commonly known extensions for ransomware encrypted files in the ES Content Update App, such as .8lock8, .encrypt, .lock93, etc.
- Based on the comparison of file names from Sysmon data with the lookup of known ransomware file extensions, this correlation search will be able to detect the ransomware attack.
- The ES Content Update App regularly updates the lookup with the latest known ransomware extensions.
Detection
Reference – From ES Content Update App – ESCU – Common Ransomware Extensions – RuleCommon ransomware notes
This tactic will find out if there are any known ransomware file names for ransomware notes present in the environment. The ransomware notes are kept by the attacker to provide a guide for the victim on how to pay for the ransom and how they will get their data back.
Data Collection
We’ll be using Sysmon data for this as well.
Thought Process
- This detection query is based on the Filesystem dataset from the Endpoint data model.
- There is a lookup of commonly known names of ransomware notes file in the ES Content Update App like HELP_TO_SAVE_FILES.txt, READ IF YOU WANT YOUR FILES BACK.HTML, etc.
- Based on the comparison of file names from Sysmon data with the lookup of known ransomware notes, this correlation search will be able to detect the ransomware attack.
- The ES Content Update App regularly updates the lookup with the latest known ransomware notes.
Detection
Reference – From ES Content Update App – ESCU – Common Ransomware Extensions – Rule
High number of file writes
How does ransomware work?
It identifies important files in the system and then encrypts those files into a new file and removes the original files. Knowing what it does, we understand that ransomware has to write a lot of encrypted files in the system. This will create a spike in the number of files being written to the system, which is another way we can identify the ransomware attack.Data Collection
We’ll be using Sysmon data for this as well.Thought Process
- This detection query is based on the Filesystem dataset from the Endpoint data model.
- Query tries to detect outliers in the number of files being written in the system.
- How does it detect the outlier/spike?
- It identifies the number of files being written in any one-hour span.
- It calculates the below items:
- Previous (prior to today) avg. write count = avg
- Previous (prior to today) standard deviation write count = stdev
- Maximum write count today = count
- Then it will calculate upper bound.
- Upper bound = (avg+stdev*4)
- If the count (maximum write today) is more than the upper bound, then that is an outlier.
- Note: We will be adjusting these calculations as time progresses to reduce the number of false positives.
Detection
Reference – From ES Content Update App – ESCU – Common Ransomware Extensions – RuleKnown False Positives
It is important to understand that if you happen to install any new applications on your hosts or are copying a large number of files, you can expect to see a large increase in file modifications.Wineventlog clearing
Based on various published reports, the ransomware takes the step of clearing the event logs shortly after infection. This will make it difficult to investigate the attack. Searching for this can help you identify systems that may have been impacted.
Data Collection
For data collection, we’ll have to use Windows Security Eventlog data. Please make sure to install the windows add-on.
Note: You have to enable the below input stanzas in the Windows Add-on (inputs.conf).
[WinEventLog://Security]
[WinEventLog://System]
Thought Process
- This detection query is based on the WinEventLog data.
- wineventlog_security` – Index/indexes for wineventlog security data. (Macro definition – see below)
- wineventlog_system` – Index/indexes for wineventlog system events. (Macro definition –see below)
- EventIDs used here:
- EventID=1102 – WinEventLog (audit log) was cleared
- EventID=1100 – WinEventLog is disabled
- EventID=104 – The log file was cleared
Detection
Reference – From ES Content Update App – ESCU – Common Ransomware Extensions – Rule
Known False Positives
These logs may be legitimately cleared by Administrators.
Macros
What are macros?
Search macros are reusable chunks of Search Processing Language (SPL) that you can insert into other searches. Search macros can be any part of a search, such as an eval statement or search term, and do not need to be a complete command. You can also specify whether the macro field takes any arguments.
How to find/update macro definition?
- Select Settings > Advanced Search > Search macros.
- Check the App is correct that you are looking at. If you don’t know the App, just select All.
- Type the macro name in the text filter and hit enter. That way you will be able to find the macro.
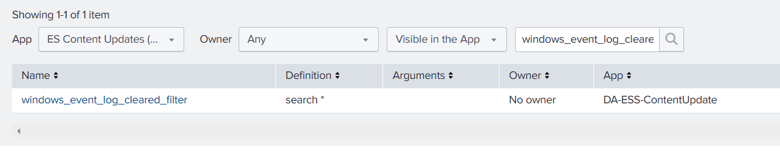
- Click on macro from the list.
- View/Edit the definition of macro in the opened Window.
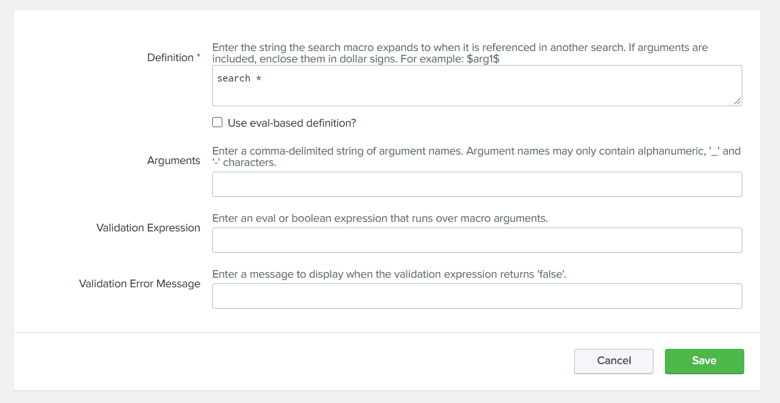
- Click Save to save your search macro
This concludes our searches for this post. The macros definitions below are used in case you don’t have Enterprise Security licensing.
Happy Splunking!
Written by Usama Houlila.
Any questions, comments, or feedback are appreciated! Leave a comment or send me an email to uhoulila@cr.jlizardo.com for any questions you might have.




